Meetup happened at Google Fremont.
Although there were other presentations, i could only participate the following:
1. Aqua: As there are ongoing security concerns regarding with Docker/MicroServices approaches, as a response, i see various solutions to that. After my initial bias that Aqua is YADSC(Yet-another Docker Security Scanning), i realized it has other capabilities as well. Beside the CVE scan, it has also
- Container Inspection which actively checks suspicious behaviour
- Fingerprint the image from dev to production, preventing spoofing
- Multiregistry support like ECR, GCR, Quay, JFrog…
- Anomality Detection on containers
- Prevent malicious behaviours
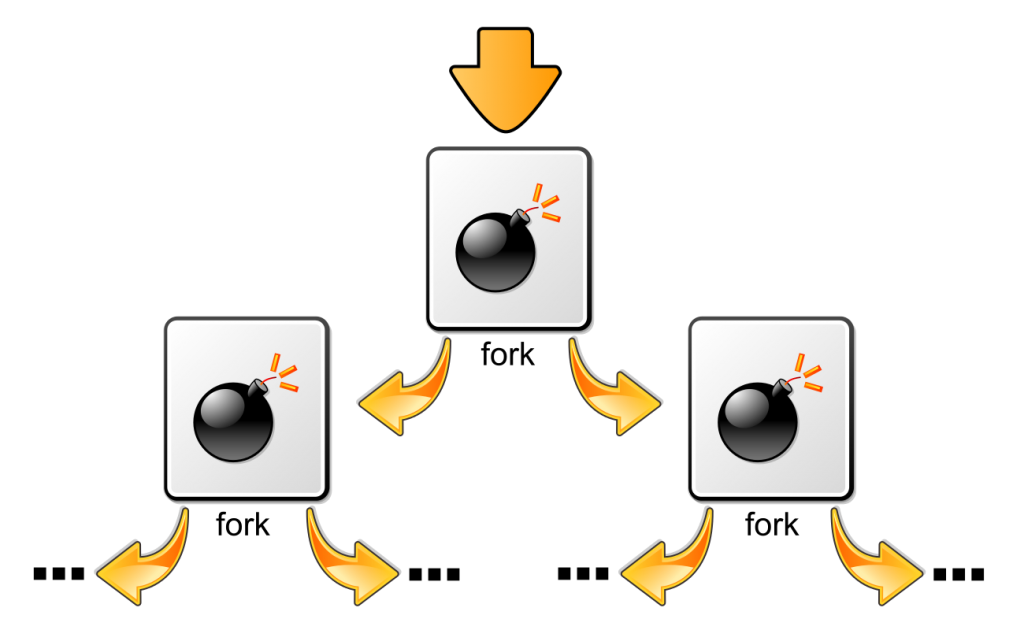
Demo regarding to malicious behaviour was fork-bomb
which is also known-as
:(){ :|:& };:
If you enter this command on your bash, you will see the effect, no responsibility is accepted:)
@chernymi demonstraited the effect of fork-bomb and container freezed, after we saw that Aqua can handle this anomality.
2. rktnetes: @wobscale beginned with explaining what is rkt and differentiation with docker, going deeper with Stage1-2-3 approach of rkt.
He continued pointing out the SPOF of dockerd for <1.11 and continerd for >=1.11
Finally, he started to explain rkynetes, which basically use rkt as the container runtime.
Some of the benefits can be summarized as
- There is no daemon running the containers
- Works with systemd
- runc is supported:)
- features/speed competes with kubernetes:
Official release seems to be coming with Kubernetes 1.3
As a summary, Kubernetes is creating its own ecosystem as well. Especially for the ones using GCP, as Google Container Engine is kubernetes, it makes sense to go with.